Ransomware: How to avoid extortion
We have attended a Webinar so you don’t have to, and you can find our notes below. In this case it was presented by Infosecurity Magazine, specifically Chris Merritt from Lumension and John Walker, a professor at the School of Science & Technology at the University of Nottingham, and was all about ransomware which is a nasty type of malware that gets on your system and then charges you to get rid of it. More recently crypto-ransomware has come to the fore. This encrypts your files, so you can’t access them, and then charges you a large sum to get them unencrypted again.
Firefly IT Solutions Ltd can help you with further info on any of the notes below, simply email helpdesk@fireflyits.com if you have any questions.
Stats and info:
- Ransomware was first heard of in around 1990
- The number of ransomware infections tracked by McAfee in Q1 2015 was around 700,000 compared to 275,000 in Q4 2014
- Over one third of firms in the UK has been hit by ransomware
- 31% of UK companies would pay the ransom to get their data back (highly controversial!)
- In reality 41% of victims admit to paying up
- Delivery of ransomware is via phishing, drive-by download from compromised websites, malvertising, botnets and malicious apps
- Often relies on vulnerabilities in operating systems or apps
- Ransoms vary from $300-$500 for home users or tens of thousands of dollars for enterprises
- Generally if you pay you will get your data back as this reinforces the business model that the criminals are using. Note “generally” not “always” as you don’t always get what you pay for!
- Payment is via bitcoins, a digital and untraceable currency
- Many pieces of malware are more than one year old and target old vulnerabilities that people could have patched
- Ransomware was defined by both presenters as evil
- Apple devices are as susceptible as any other devices. Do not assume you are safe because you have a mac or iPhone!
What can you do? I have highlighted the most cost effective methods that a small business may afford to employ below, but unfortunately none of them are 100% effective, even when used in combination. Having any of them is more effective than having none.
- Endpoint defences (be proactive!):
- Manage your patches and configuration
- Application whitelisting – a list of programmes that are allowed to run on your system
- Data encryption – often the data is stolen before it is encrypted. This protects you against it being stolen, not against it being encrypted again.
- Device control – Stop your employees connecting uncontrolled devices to your systems and networks as they can be sources of infection.
- Antivirus
Preparation. You should all be doing all of these:
- Backups: 3 copies of any file, two on different types of media and one off-site. Know which files are the most important to you and look after them.
- Staff training: Any IT staff should know how to deal with an infection
- User training: First line of defence and they need to understand what ransomware is, not to click on attachments, to pay attentions to warnings etc.
Here are actions you should consider post infections:
- Your configuration and restore procedures (incident response plan)
- Forensics: How did the infection happen and what can be done to avoid it happening again
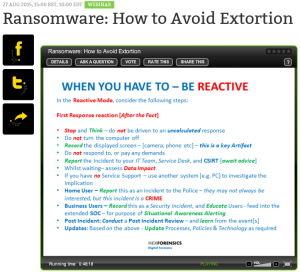
- See the picture at the top of this article for some excellent recommendations on actions to take once infected
If you think this webinar sounds interesting then visit www.infosecurity-magazine.com as they do them regularly on a variety of topics.
You must be logged in to post a comment.